In an alarming development, cybercriminals have devised a new method to circumvent Apple’s built-in phishing protection for iMessage, potentially exposing you to malicious links and scams. This sophisticated tactic exploits a security feature designed to protect you, turning it into a vulnerability that could lead to significant personal and financial risks.
I’M GIVING AWAY THE LATEST & GREATEST AIRPODS PRO 2
Enter the giveaway by signing up for my free newsletter.
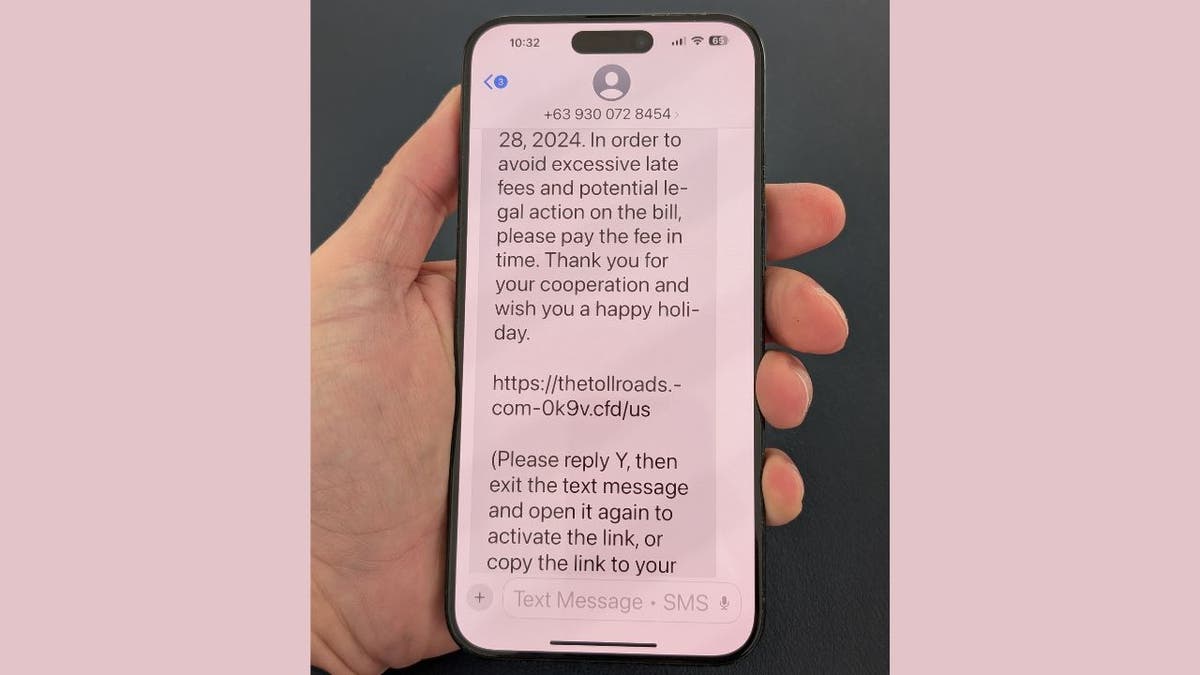
Scammer’s phishing text message sent to iPhone (Kurt “CyberGuy” Knutsson)
The trick unveiled
Apple’s iMessage automatically disables links in messages from unknown senders as a security measure. However, cybercriminals have found a way to exploit this protection. By instructing you to reply to the message, often with a simple “Y,” the attackers can re-enable previously disabled links. This seemingly innocuous action not only activates the links but also signals to the scammers that they’ve found an engaged target for future attacks.
We reached out to Apple for a comment but did not hear back before our deadline.
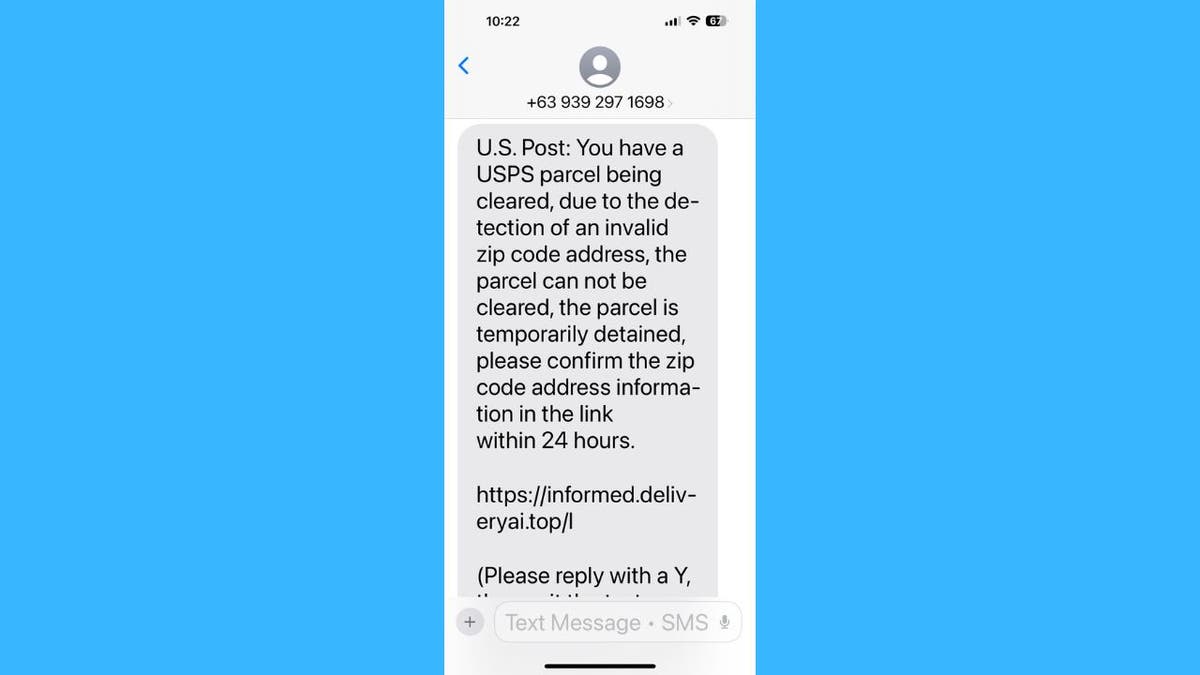
Scammer’s phishing text message sent to iPhone (Kurt “CyberGuy” Knutsson)
HOW TO PROTECT YOUR IPHONE & IPAD FROM MALWARE
Common phishing lures
These deceptive messages often masquerade as notifications from trusted organizations, such as:
- Undeliverable packages from courier services (USPS, DHL, FedEx)
- Unpaid road tolls
- Outstanding payments or fees
The messages typically end with instructions like: “(Please reply Y, then exit the SMS, re-open the SMS activation link, or copy the link to open in Safari).”
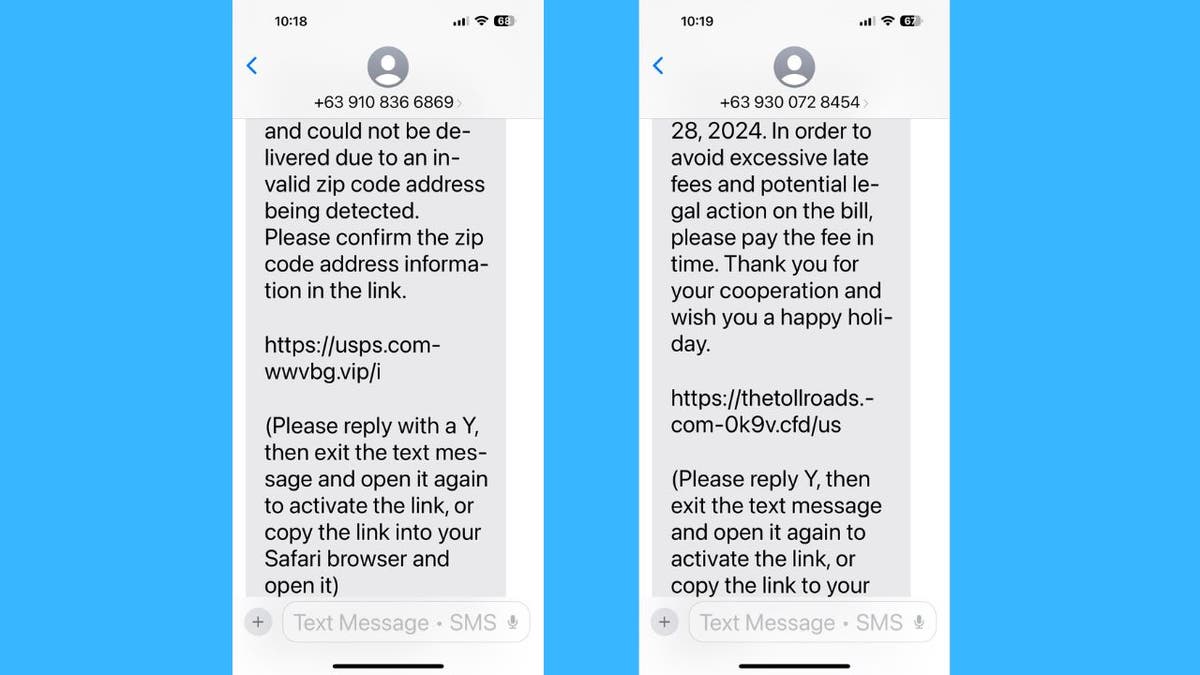
Scammer’s phishing text messages sent to iPhone (Kurt “CyberGuy” Knutsson)
THE ONE SIMPLE TRICK TO HELP KEEP OUT CYBER CREEPS ON IPHONE
The rising threat of smishing
This new tactic is part of a broader trend of smishing (SMS phishing) attacks targeting mobile users. With the increasing reliance on smartphones for various activities, including financial transactions and personal communications, these attacks pose a significant threat to users’ security and privacy.
DOES MY IPHONE NEED ANTIVIRUS PROTECTION?
How to protect yourself
To safeguard against these sophisticated phishing attempts, consider the following steps.
1) Never reply to suspicious messages: Avoid responding to texts from unknown senders, especially those asking you to reply to activate links. Additionally, make sure to delete suspicious text messages and block the sender to prevent further attempts. Since the sender is not in your contact list, you can click Report Junk at the bottom of the text. Then click Delete and Report Junk. This will report the conversation as junk by sending it to your wireless carrier and Apple using your phone number.
2) Verify sender identity: Contact organizations directly through official channels if you’re unsure about a message’s legitimacy.
3) Be skeptical of urgency: Scammers often use urgent language to prompt quick, thoughtless actions.
4) Enable message filtering: Use your device’s built-in filtering options to sort messages from unknown senders. Here are the steps:
- Open Settings
- Scroll down and click Apps
- Tap Messages
- Turn on Filter Unknown Senders
This feature allows you to automatically sort messages from unknown senders, easily filter unread messages and manage your message inbox more efficiently.
5) Use two-factor authentication (2FA): 2FA adds an extra layer of security to your accounts by requiring a second form of verification, such as a text message or authentication app, in addition to your password. This significantly reduces the risk of unauthorized access, even if your password is compromised.
6) Have strong antivirus software: The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2025 antivirus protection winners for your Windows, Mac, Android and iOS devices.
7) Invest in personal data removal services: By reducing your online footprint, you make it harder for cybercriminals to obtain your contact information, potentially preventing them from sending you these deceptive iMessage phishing texts in the first place. While no service promises to remove all your data from the internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check out my top picks for data removal services here.
What to do if you’ve been targeted
If you suspect you’ve fallen victim to a smishing attack:
- Report the incident to relevant authorities and institutions
- Freeze your credit to prevent potential identity fraud
- Change passwords and PINs for all your accounts; consider using a password manager to generate and store complex passwords
- Monitor your finances and online accounts for suspicious activity
- Use an identity theft protection service: Identity theft companies can monitor personal information like your Social Security number, phone number and email address and alert you if it is being sold on the dark web or being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals.
One of the best parts of some identity theft protection services is that they have identity theft insurance of up to $1 million to cover losses and legal fees and a white-glove fraud resolution team where a U.S.-based case manager helps you recover any losses. See my tips and best picks on how to protect yourself from identity theft.
Kurt’s key takeaways
This latest trick targeting iMessage users serves as a reminder that even seemingly secure systems can be vulnerable to social engineering. By remaining cautious and following best practices for digital security, you can significantly reduce your risk of falling victim to these sophisticated phishing attempts.
What other cybersecurity challenges have you encountered with your mobile devices, and what questions do you have for us? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you’d like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
New from Kurt:
Copyright 2024 CyberGuy.com. All rights reserved.


